Cyber Security:
A random value (called the salt) is added to the plaintext password before the hashing process. This greatly increases the number of possible hash values for the password and means that even if two people choose identical passwords, their hashed passwords have completely different values. The hashed password and the relevant salt are both stored by the password server. When the user attempts to log in to the computer, their password and the salt are added together, hashed and compared to the stored, hashed value. Salting is only effective if:
For instance, the passwords used by UNIX in the early 1970s were restricted to eight characters and used a 12-bit salt. When released this was secure enough – it was not feasible to generate the hashes for every possible password each of which had been salted with all 4,096 possible salts. However, the rapid advance in computer power and storage capacity meant that longer salts are required. A typical piece of advice is that the salt should be the same length as the output of the hashing function – so if your hashing function generates 256-bit hashes, a different 256-bit unique salt should be used for each password. |
|

Custom Search
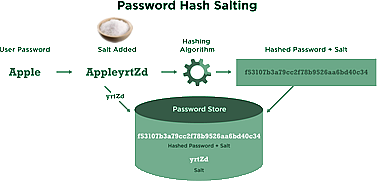 Salting is a way of increasing the security of stored passwords.
Salting is a way of increasing the security of stored passwords.

