Cyber Security: Passwords
 Identification and authentication
Identification and authentication

 Passwords before the computer age
Passwords before the computer age
Passwords have long been used to identify and authenticate people.
In Western history, the concept of the password can be traced as far back as the so-called "shibboleth incident" in the 12th chapter of the biblical Book of Judges. In the chaos of battle between the tribes of Gilead and Ephraim, Gileadite soldiers used the word "shibboleth" to detect their enemies, knowing that the Ephraimites pronounced it slightly differently in their dialect.
12th chapter of the biblical Book of Judges. In the chaos of battle between the tribes of Gilead and Ephraim, Gileadite soldiers used the word "shibboleth" to detect their enemies, knowing that the Ephraimites pronounced it slightly differently in their dialect.
A famous password appears in the classic tale "Ali Baba and the Forty Thieves," invented in the 18th century by the French Orientalist Antoine Galland. "Open, Sesame!" was a password used to open a magically sealed cave. This password is well known and used in many contexts.
Giving a password is important to identify fellow conspirators and to enter premises held by spies and plotters. When the Houses of Parliament were to be blown up by Catesby and his crew, passwords and cypphers would have played an important part in their communications.
 What is the function of a password?
What is the function of a password?
 A password works in two ways, it:
A password works in two ways, it:
 protects information from being accessed by those who have not been given the right to do so
protects information from being accessed by those who have not been given the right to do so
 authenticates those having a right to access the information.
authenticates those having a right to access the information.
Billions of people use online services every day, and it is crucial that systems prevent users from accessing information they are not entitled to, yet allows those who are entitled to easily gain access to the information.
To do this, we need a way of uniquely identifying each user that prevents users from impersonating each other.
Passwords and passcodes are the most common way of authenticating users.
When opening an account you will be asked to supply a password.
 PIN (Personal Identifier Number)
PIN (Personal Identifier Number)
These are commonly found for use with a credit or debit card.
They are also used within a digital pad access system - instead of key access - to buildings and rooms.
They use two-factor authentication.
 Ideal Password
Ideal Password
An ideal password must satisfy two conflicting aims.
It should be:
 memorable enough that the user can recall it without writing it down
memorable enough that the user can recall it without writing it down
 long enough and unique enough that no one else can guess it.
long enough and unique enough that no one else can guess it.
 containing upper and lower case letters, numbers and symbols. (see Brute Force Hacking)
containing upper and lower case letters, numbers and symbols. (see Brute Force Hacking)
Click here to go to a page dedicated to choosing a 'secure' password.
If the password is transmitted from the user to the server as simple text – it could be intercepted as it travels across the network.
However if we encrypt the communication between the user and the server, we make it more difficult for a hacker.
 Storing passwords for authentication of a user
Storing passwords for authentication of a user
If a password is stored on a server as plaintext then if hacked all the passwords for all the users of the system would be instantly revealed.
But when a user enters a password the server needs to be able to confirm that this is the correct password for that user before it grants access.
This second problem can also be solved using a technique called hashing.
A 'hash with salt' is the result of processing plaintext to create a unique, fixed length identifier that cannot be used to reconstruct the original data – even if the hash falls into hostile hands.
In this scheme, a hashing function is used to create a hash of a password, which is stored on the server – the password itself is discarded. When the user enters a password, this is sent over the network and hashed on the server using a copy of the same hashing function.
The resulting hash is compared to the hash stored on the password server.
Only if they match will the user be granted access.
Some implementations of this scheme will hash the user's password before sending it across the network to be compared with the hash stored on the server.
Almost all online services and computer systems store passwords as hashes – but surprisingly, errors still happen. The problems described in the following case study could have been avoided if hashing had been used.
 Is your password easy to be hacked?
Is your password easy to be hacked?
Weak passwords could threaten the security of digital information you hold and make it easy for your online identity to be stolen. It is a good idea not to use just one simple password for everything. You should also regularly change your passwords. There is plenty of advice on the web for creating strong passwords - but generally they should contain a mixture of upper and lower case letters, some numbers and symbols.
You may get informed by the company concerned if a data breach occurs, and asked to change your password - but there is a very useful site that will inform you of security breeches that contain your email even if the company does not inform you.
You can check and see whether your account has been part of a reported data breach that included your email address by visiting:
https://haveibeenpwned.com
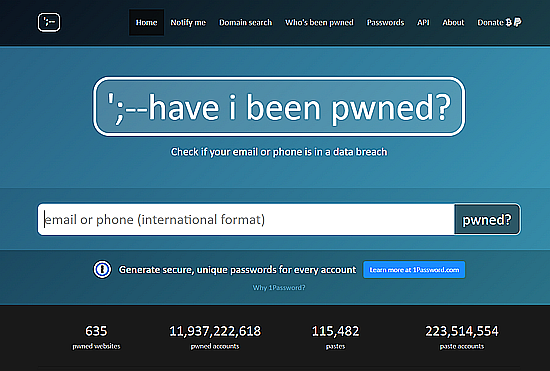

"Pwned" is a corruption of the word "Owned."
This originated in an online game called Warcraft, where a map designer misspelled "owned."
When the computer beat a player, it was supposed to say, so-and-so "has been owned."
Instead, it said, so-and-so "has been pwned."
It basically means "to own" or to be dominated by an opponent or situation, especially by some god-like or computer-like force...  |
 Is my password 'out there' on the Dark Web?
Is my password 'out there' on the Dark Web?
You can also use this site to check whether a password that you use has also been found in a data breach visit.
 Don't type in a complete password to start with.
Don't type in a complete password to start with.
 Type in the first few characters and click 'pwned?'
Type in the first few characters and click 'pwned?'
 If it doesn't come up, your password is safe.
If it doesn't come up, your password is safe.
 If it does get a match, add the next character and check again.
If it does get a match, add the next character and check again.
 If you have typed in the complete password and get a match it is most definitely time to change your password!
If you have typed in the complete password and get a match it is most definitely time to change your password!
 How to measure the strength of a password
How to measure the strength of a password
(This section was extracted from the free online OU Cyber-Security Course - I strongly recommend you try it!)
Think about why the security of passwords and what makes a very strong password.
Things to consider include:
 password length
password length
 the range of characters you used
the range of characters you used
 whether any personal information is recognisable in your passwords (and could be guessed)
whether any personal information is recognisable in your passwords (and could be guessed)
 how easy or difficult it is for you to remember the new password.
how easy or difficult it is for you to remember the new password.
Now have a play with a program that shows you how they calculate whether your password is weak or strong.
 To start, open the password strength checker.
To start, open the password strength checker.
 Now construct a password using the place name of the city, town or village where you live using only lower case letters – no capitals, spaces, dashes, and so on. If you live in a place with a short name such as Ayr, you will need to repeat the name a few times until you have met the minimum length requirement for the password checker.
Now construct a password using the place name of the city, town or village where you live using only lower case letters – no capitals, spaces, dashes, and so on. If you live in a place with a short name such as Ayr, you will need to repeat the name a few times until you have met the minimum length requirement for the password checker.
 Then test it and make a note of the score.
Then test it and make a note of the score.
 Open the link again - in a new window each time so that you can refer back to it as you continue with this section - and modify your password into a very strong password using the techniques for converting a phrase into a password that you learned earlier. See how complex you can make it while it is still memorable.
Open the link again - in a new window each time so that you can refer back to it as you continue with this section - and modify your password into a very strong password using the techniques for converting a phrase into a password that you learned earlier. See how complex you can make it while it is still memorable.
 |
If you need to remember a host of passwords (remember - it is advised to have a different one for each account!) then you may want to consider using a password manager. |
What happens if you cannot enter your password?
Secure encryption and secret passwords can result in some significant problems for your business or family should you suddenly become incapable of handling these procedures (say, because you have a stroke or an accident which incapacitates you) or should you die.
Business owners need to analyse how their business would continue to have access to any business documents and systems while ensuring full security at all times.
Everyone needs to evaluate what assets should remain inaccessible on their death, and which assets should be available to family or friends. For the latter, the process by which secure passwords can be passed on to others needs to be carefully planned.
 Is my password 'out there' on the Dark Web?
Is my password 'out there' on the Dark Web?Don't type in a complete password to start with.
Type in the first few characters and click 'pwned?'
If it doesn't come up, your password is safe.
If it does get a match, add the next character and check again.
If you have typed in the complete password and get a match it is most definitely time to change your password!
 How to measure the strength of a password
How to measure the strength of a password password length
the range of characters you used
whether any personal information is recognisable in your passwords (and could be guessed)
how easy or difficult it is for you to remember the new password.
![]() To start, open the password strength checker.
To start, open the password strength checker.![]() Now construct a password using the place name of the city, town or village where you live using only lower case letters – no capitals, spaces, dashes, and so on. If you live in a place with a short name such as Ayr, you will need to repeat the name a few times until you have met the minimum length requirement for the password checker.
Now construct a password using the place name of the city, town or village where you live using only lower case letters – no capitals, spaces, dashes, and so on. If you live in a place with a short name such as Ayr, you will need to repeat the name a few times until you have met the minimum length requirement for the password checker. ![]() Then test it and make a note of the score.
Then test it and make a note of the score. ![]() Open the link again - in a new window each time so that you can refer back to it as you continue with this section - and modify your password into a very strong password using the techniques for converting a phrase into a password that you learned earlier. See how complex you can make it while it is still memorable.
Open the link again - in a new window each time so that you can refer back to it as you continue with this section - and modify your password into a very strong password using the techniques for converting a phrase into a password that you learned earlier. See how complex you can make it while it is still memorable.

 Identification and authentication
Identification and authentication
 12th chapter of the biblical Book of Judges. In the chaos of battle between the tribes of Gilead and Ephraim, Gileadite soldiers used the word "shibboleth" to detect their enemies, knowing that the Ephraimites pronounced it slightly differently in their dialect.
12th chapter of the biblical Book of Judges. In the chaos of battle between the tribes of Gilead and Ephraim, Gileadite soldiers used the word "shibboleth" to detect their enemies, knowing that the Ephraimites pronounced it slightly differently in their dialect.  A password works in two ways, it:
A password works in two ways, it:


