Cyber-Security - C.I.A
|
C |
I |
A |
Confidentiality |
Integrity |
Availability |
Data to be read by only the right people |
Data only be changed by authorised people or processes |
Data to be available to read and use whenever we want |
 Confidentiality
Confidentiality
In order to safeguard the confidentiality of data special training must be given to those within a company that have access to sensitive documents.
Training should:
familiarize authorized people with the risks involved with failing to safeguard confidentiality and how to guard against them.
teach about the importance of employing strong passwords and password-related best practices.
explain the dangers of 'bending the rules' on data-handling by getting employees to study the potentially disastrous results of staff 'taking shortcuts'.
The company should set up procedures that shepherd their employees into safe routes when handling customer data and put in place procedures for customers to follow when accessing their data that safeguards confidentiality.
Methods used to ensure confidentiality:
User IDs and passwords
2FA - two-factor authentication
Biometric verification
Security tokens, key fobs or soft tokens.
Minimising the number of places where sensitive information appears.
Minimise the number of times data is actually transmitted to complete a required transaction.
Confidentiality of extremely sensitive documents
Extra measures might be taken in the case of extremely sensitive documents.
They should be stored only on air-gapped computers and disconnected storage devices to minimise the chance of being compromised by hackers.
Highly sensitive information should be stored in hard-copy form only.
 Integrity
Integrity
Measures to protect integrity include file permissions and user access controls.
Version control may be used to prevent erroneous changes or accidental deletion by authorized users from becoming a problem. In addition, organizations must put in some means to detect any changes in data that might occur as a result of non-human-caused events such as an electromagnetic pulse (EMP) or server crash.
Data might include checksums, even cryptographic checksums, for verification of integrity. Backups or redundancies must be available to restore the affected data to its correct state. Furthermore, digital signatures can be used to provide effective nonrepudiation measures, meaning evidence of logins, messages sent, electronic document viewing and sending cannot be denied.
It is important to be able to distinguish between these three aspects of security.
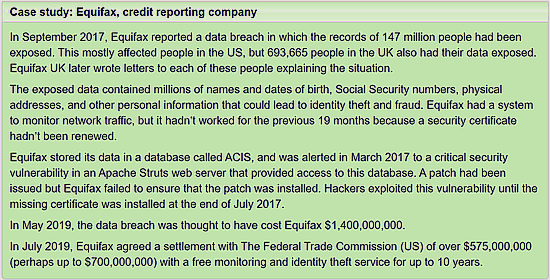
So let’s look at an example. This example comes from the Open University Site:
We need to consider each aspect separately:
| C | Confidentiality was certainly violated! Unauthorised people could read the data. | |
| I | Integrity however, was preserved because the data was not changed. | |
| A | Availability also was still intact - authorised users still had full access to the data. |
So only one of the three aspects was breeched.... still cost the company a fortune though!



